New Lock screen bug bypasses iPhone/iPad passcode, lets you see photos/contacts
Apple likes to pride itself with strong security in iOS, but for all the platitudes the fact remains that the iPhone’s Lock screen is one of iOS’s weakest links. And now, YouTuber iDeviceHelp has discovered a new Lock screen vulnerability that lets anyone in possession of your iPhone bypass the passcode and get to your contacts and photos. The bug has been reported to Apple and should be fixed in a future update.
The trick involves calling another person’s mobile phone number via FaceTime or cellular and tapping the Message option on their device to get to the Messages screen.
From there, you’ll use Siri to enable VoiceOver which lets you exploit the vulnerability and gain access to the Photos library and contacts. The method is a bit finicky as you’ll need to get the timing of your taps right but once you get the hang of it, it’ll work like a charm.
After a few tries, I was able to successfully reproduce the steps outlined in EverythingApplePro’s how-to video to confirm that it works as advertised on an iPhone 7 running iOS 10.1.1. I could browse all of the photos even though the phone was locked the whole time.
[youtube https://www.youtube.com/watch?v=hP3BMyrFBSs?feature=oembed&w=500&h=281]
How to unlock any iPhone photos without a passcode
1) Press and hold the Home button on the device you want to break into and ask Siri, “Who am I?”. A contact card goes up letting you see a person’s mobile phone number and any email addresses associated with iMessage (if they disabled Siri access on the Lock screen, you’ll be out of luck).
2) From your own iPhone, iPad or iPod touch, launch FaceTime and call the persons’s number.
3) When their device starts ringing, tap the Message option on the Lock screen and select the option in the popup menu labeled Custom…
4) A Messages sheet pops. You’ll notice that the TO field is pre-populated with the caller’s contact information. Now press and hold the Home button and ask Siri to “Turn on VoiceOver”.
5) With the VoiceOver feature turned on, double tap the TO field at the top with the caller’s information, then immediately tap anywhere on the keyboard. Make sure you double tap the empty section, not the name.
You want the three icons (Camera, iMessage Apps and App Store) on the left of the Messages text field to appear right after tapping the keyboard. It’ll certainly take a few tries until you get this right.
After the icons show up, VoiceOver’s focus should remain on the TO field at the top.
6) If you see both a black rectangle around the TO field and the three icons to the left of the Messages text field, invoke Siri again and tell her to “Disable VoiceOver”.
7) Due to a bug in iOS, anything typed on the keyboard at this point will be directed to the TO field where it shouldn’t really be sent. This has some unintended consequences, as you’ll see later. Now tap a key, any key on the keyboard and see if Messages displays any matching contacts with an “i” icon next to them.
If not, tap another key and so forth.
8) Tap “i” next to a contact to get to their full contact card.
9) You’re on the contact card screen. Now scroll down and tap Create New Contact.
10) On the New Contact screen, tap Add Photo below the mugshot icon, then tap Choose Photo. And there you go: you’ve just accessed all of the photos on the person’s iPhone, without a passcode.
If you inspect the iOS status bar closely, you should see the padlock icon.
Although the device is locked, you can tap All Photos or Camera Roll to see the complete Photos library. You can even see their Recently Deleted album and browse their hidden shots and videos.
Of course, we don’t expect anyone to exploit this vulnerability for nefarious purposes aside from perhaps pranking your friends or making sure your significant other is not cheating on you.
Just kidding, we do not condone privacy breaches of any sort. The contents of any person’s iPhone are their business, not yours. Just because there’s a bug in iOS that makes it possible to bypass the Lock screen doesn’t mean you should take advantage of it and sniff around other people’s phones.
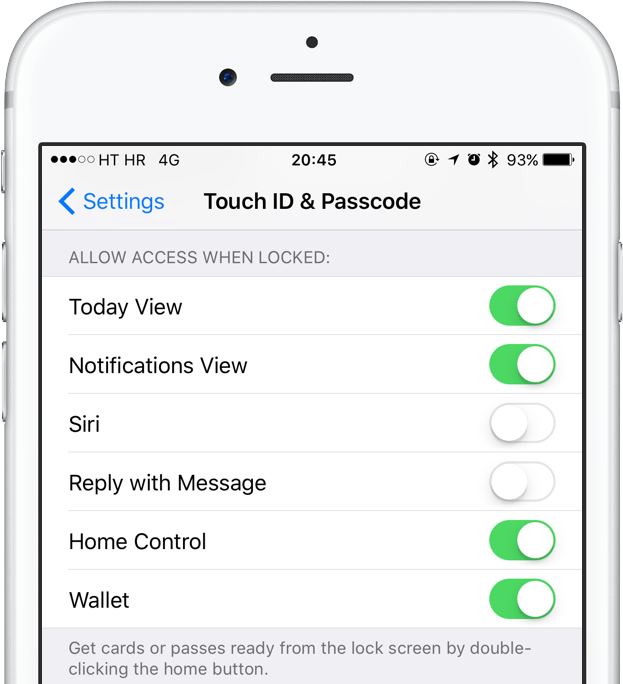
Obviously, you can protect yourself quite easily from this bug until a patch is released—just disable access to Siri and the Reply with Message feature from the Lock screen. Go to Settings → Touch ID & Passcode and slide Siri and Reply with Message toggles below the Allow Access When Locked headline to the OFF position.
This should ensure that no one will be able to invoke Siri on the Lock screen to find out your mobile phone number or use the Message option when the phone call comes in to get to your photos.
As mentioned, this significant security leak has already been reported to Apple and is likely going to be fixed in a future iOS software update. So how far back does this go? According to the poster, the vulnerability is exploitable on the latest iOS 10.2 beta 3 as well as iOS builds for older devices.
It even works on iPads and the iPhone 4s.
That’s kinda of a big deal because Apple officially no longer supports the iPhone 4s meaning it stopped releasing any updates for it beyond iOS 9.3.5. However, this newly found Lock screen bypass will likely be fixed for iPhone 4s owners in the form of iOS 9.3.6 or a quick emergency update.
Have any of you guys ben able to reproduce this obvious bug in iOS?
And if so, what did you think of it?
Source: iDeviceHelp on YouTube
Source link: http://www.idownloadblog.com/2016/11/17/lock-screen-bug-bypasses-iphoneipad-passcode-lets-you-see-photoscontacts/



Leave a Reply